As a busy social media leader, your team uses Agorapulse to make managing multiple social media accounts or an expanding social media presence with thousands of followers, influencers, and engagements easier. After all, with myriad social accounts, networks, engagements, followers, comments, and messages to manage, the amount of data that your team will be handling daily is huge.
But when you consider that 510,000 comments are posted and 293,000 statuses are updated every single minute, on Facebook alone, and that 20% of social media accounts are likely to get hacked at some point, how can you be sure that the data that’s being captured, processed, and stored in your Agorapulse platform is safe, secure, and protected from all evil?
I’ll tell you how!
What Data Security Really Means
First, let’s clear something up. Data security is not the same as data privacy.
Data privacy is about keeping data confidential. So, we’re talking third-party cookies and data encryption. Data security is about protecting data from malicious activity, such as data corruption, data breaches (intentional and unintentional), data theft, and unauthorized access to data.
You know, the stuff that makes it into the news:
“Yahoo Says Hackers Stole Data on 500 Million Users” (New York Times)
“Stolen Data of 533 Million Facebook Users Leaked Online” (Business Insider)
How Can Data Be Protected From Malicious Activity?
“Data security is the practice of protecting digital information from unauthorized access, corruption, or theft throughout its entire lifecycle.” (IBM)
Because you head up such a busy social media team, you are ultimately responsible for a lot of highly sensitive data. The buck stops with you.
Data security and data governance must, therefore, be at the forefront of everything you do, everything your team does, and everything that any third-party tool that you use does too.
Agorapulse has been built with data security in mind, from the way that data is captured and stored within the platform, to the administrative and access controls it has built into its features. Data security is a priority for us. We even have specific organizational processes and policies in place to ensure that when you’re using our social media management tool, your data is safe.
Read why cybersecurity experts at Kaspersky trust Agorapulse for secure social media management
More on Agorapulse and its water-tight data security measures to come. First, it’s time for some home truths.
The Biggest Data Security Issues That You and Your Team Will Face
As you’re reading this,one or more of the following data security issues will be happening around you …
Accidental exposure
Data breaches are the result of malicious attacks from sophisticated hackers. But more than 40% of data security leaks are caused by employee negligence.
Any member of your social media team could easily expose data to cyber-criminals, without even knowing. They could download confidential data onto a personal storage device, for example, or send sensitive information via email to another colleague.
Remember the monumental mess-up during the 2017 electoral vote between Donald Trump and Hilary Clinton? An employee who worked for a marketing company that was hired by the Republican National Committee shared internal documents on a publicly accessible Amazon server and exposed the information from over 200 million registered voters.
Data loss in the cloud
A whopping 91% of businesses use the cloud to run applications, store data, and make sharing information and collaboration easier and more cost-effective. Agorapulse included.
But when data is in the cloud, it’s harder to control and keep secure. If proper data security controls aren’t put in place to secure the cloud environment, hackers will access data that’s stored in the cloud from personal devices and over unsecured networks. It’ll become all too easy to share information with unauthorized parties and data will, therefore, be exposed to cyber threats such as:
- Ransomware
- Malware
- Phishing
Something as simple as uploading a file with private data in it onto a cloud service and forgetting to protect it with a password is enough to leave it open to malicious intent.
SQL injections
This one sounds technical, and it kind of is. But you don’t need to know how to code to understand how it works and why it accounts for over 50% of all web application attacks.
A SQL injection (or SQLi as it’s known) is a technique used by hackers to gain unauthorized access to data. Basically, these hackers will hack into production, testing, or live environments and add a line of malicious code that exposes customer data or gives attackers administrative access so they can take over. SQLis are usually the result of bad, lazy, and insecure coding practices.
Data Security Best Practices: What May Happen If You Don’t Follow Them
“It’s not enough to protect your own valuable company information anymore; you must also take adequate security measures to protect all the information entrusted to you.” – Forbes
Following on from the above, on average, data security is compromised every 39 seconds. So, in the time that it takes one of your team to post on Facebook, somebody has breached a data security protection measure and either accidentally exposed sensitive data or gained unauthorized access to confidential information.
In response to this alarming fluctuation in data breaches, over the last decade or so, businesses have been working hard to develop, upgrade, and upscale their data security measures. But so have cyber-criminals. They’ve leveled up their hacking abilities, so that they can break these sophisticated data security measures and exploit our data.
For instance, it was only last year, in 2021, that Facebook experienced one of its biggest cyber-attacks that affected more than 530 million users worldwide.
But if a giant like Facebook can’t stop the cyber-criminal underworld from taking over, how do you stand a chance?
Honestly? You don’t. Not really.
But you can make sure that you’re doing everything you can to keep the data that you’re responsible for as safe and secure as possible.
Data Security Features: How Agorapulse Protects Data Like It’s Their Own
We talked about three common data security issues earlier:
- Accidental exposure
- Data loss in the cloud
- SQL injections
Here’s how Agorapulse handles each one and keeps sensitive information protected from accidental or intentional exposure.
1. Agorapulse protects against accidental exposure with tight access controls
The ability to control who has access to certain information, data, or resources is a fundamental part of data security, especially when there is highly sensitive data at risk. Tight access controls and only giving specific people access to certain information, as opposed to the whole company, lowers the risk of accidental data exposure and data being accessed without proper authorization.
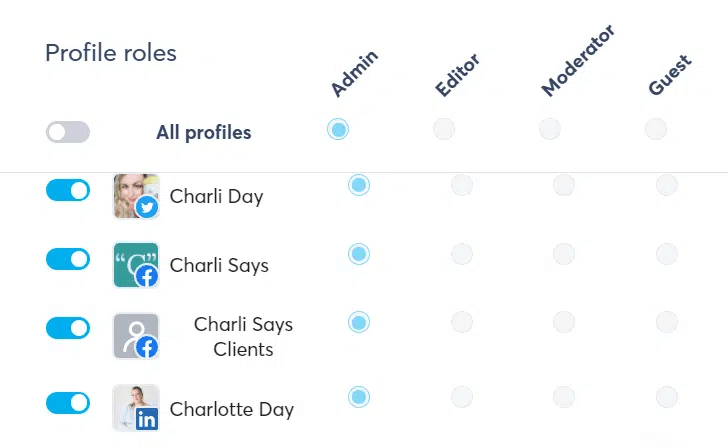
When using Agorapulse, as you probably know, every single user has an “organization role” (owner, manager, or standard member), and a “social profile” role (Admin, Editor, Moderator, or Guest).
Individual users can be given access to specific features, parts of the tool, and social media accounts, depending on their roles within the team or company.
For instance, an Owner would be able to view invoices and edit billing information, but a Manager or a Member wouldn’t. A Moderator would have full access to all Social Media Inbox and Listening features (they’d be able to approve, reply, assign, bookmark, and like comments or messages, etc.). However, a Guest would have view-only access and wouldn’t be able to perform any publishing or moderating actions.
Plus, with features like the Shared Calendars, you can get external parties to approve content without giving them access to the platform. And, with the Asset Library, you can share, send, and upload files without needing to use a third-party platform.
For a detailed overview of the various user access controls, check out the Agorapulse support page.
2. Agorapulse protects against data loss in the cloud with 2FA security measures
As we established earlier, you’re responsible for a lot of incredibly sensitive data. And a cyber attacker can easily access that data if it’s stored within a cloud environment that doesn’t have solid security measures and controls in place.
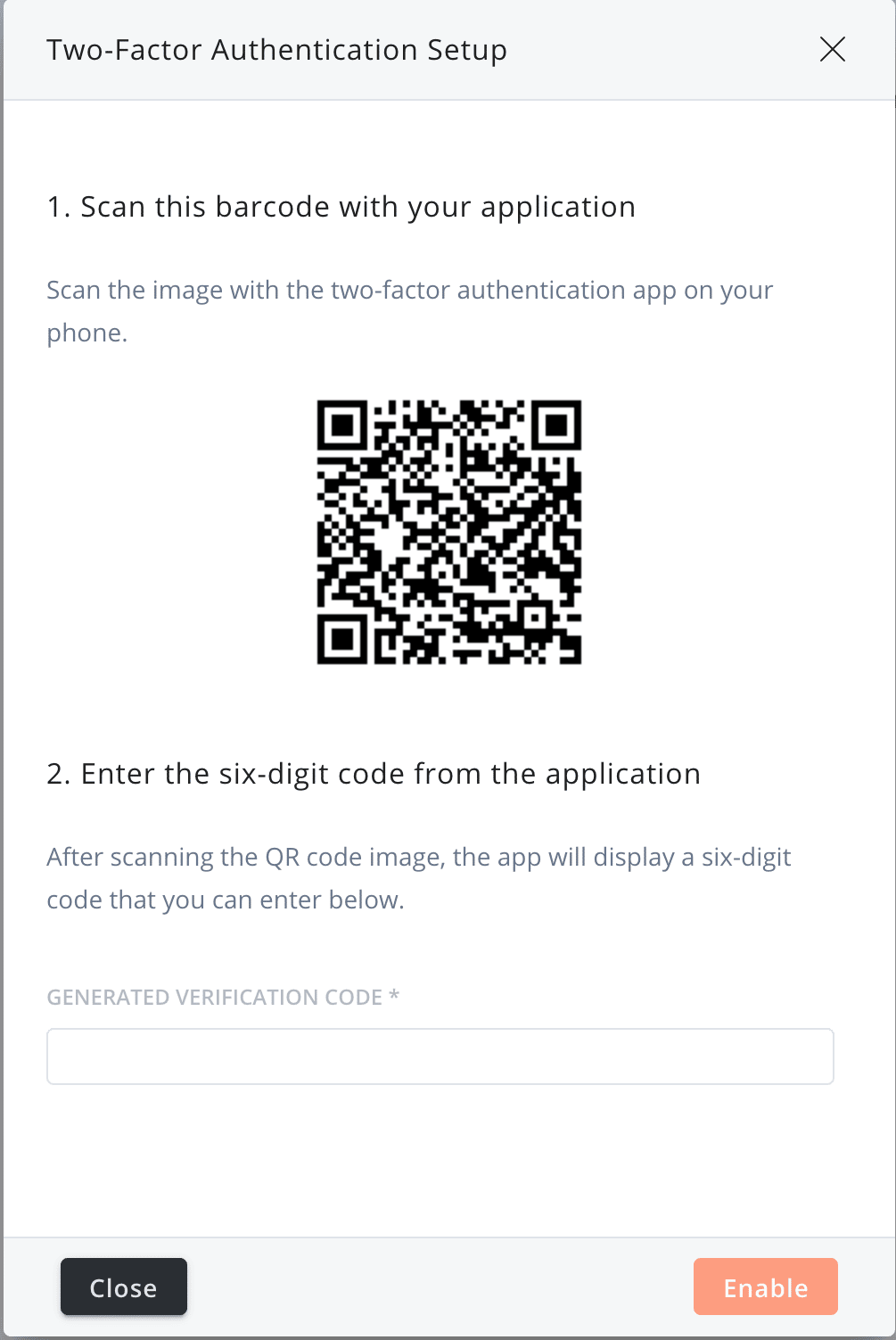
This is why we’ve built-in two-factor authentication (2FA) protocols into our social media management platform, and why we suggest that you enable it NOW (if you haven’t already)!
2FA is an extra layer of protection that will significantly reduce the risk of a cyber attack. While traditional authentication protocols do limit access to sensitive data, they don’t truly protect it.
2FA combines traditional authentication measures, like asking for a password, with a piece of information that only that user will know. For instance, when you enable 2FA, to log into the Agorapulse platform, you’ll be asked to confirm your login credentials with a 6-digit code that’s been sent to your smartphone app.
3. Agorapulse protects against SQL injections with data security protocols
Sloppy mistakes, insecure coding practices, and weak security protocols leave data wide open and vulnerable to cyber-attacks.
Not on our watch.
Firstly, we decided to host and run our cloud-based social media management platform on Amazon Web Services (AWS) because they have some of the strongest security measures in the world. These measures protect our infrastructure, and therefore your data, like Fort Knox.
Secondly, our team of developers is all in-house, we don’t trust anyone outside of the company to work on our product. Our in-house developers also monitor the application 24/7 so they can detect anomalies or potential attacks and automatically block them. Code is continuously reviewed and tested to spot mistakes and vulnerabilities.
Access to the development, production, and live environments requires both Secure Socket Shell (SSH) keys and 2FA, and only the development team has access to the production environment: Any offending IP addresses are automatically blacklisted.
Thirdly, we are an official Meta partner. To become an official Meta partner, we had to meet (and maintain) several requirements that involved making sure data security was at the forefront of all our activities and showing that we could offer added protection for the data we captured and stored in the application.
But that’s not it. Find out just how seriously we take security here at Agorapulse.
“Agorapulse respects our customers’ privacy, and keeping our customers’ data protected at all times is our highest priority.” (Security at Agorapulse, Agorapulse)
What next?
If you’d like even more reassurance about what security measures Agorapulse have implemented to protect your data, why not contact the customer support team?
Or if you’re not yet using Agorapulse but want to see how it stacks up, why not start a free trial? If you have a bigger team that has specific and complex needs, book a free demo! The team will talk you through the product features, answer all your questions, and clear up any security concerns that you may have.